|
Executive summary – Step 3 – COSO Control Activities If risk assessment is the radar that scans the horizon, control activities are the brakes and steering wheel of the organization. They are the mechanisms that allow leadership to respond to risks with precision: slowing down when approaching danger, steering around obstacles, and navigating safely on curvy and unpredictable roads. A company that invests heavily in identifying risks but neglects control activities is like a ship with radar but no rudder—able to see the iceberg but powerless to change course. Within the COSO Internal Control – Integrated Framework, control activities represent the specific actions, policies, and procedures that transform risk insights into operational reality. They serve as the guardrails that keep strategy aligned with objectives, the checkpoints that ensure compliance with regulation, and the safeguards that prevent fraud, errors, and reputational damage. These activities take many forms: segregation of duties, approval hierarchies, reconciliations, IT access controls, and physical security measures. |
Where are we? At its core, the COSO Internal Control Framework identifies five integrated components:
These five components function as an integrated system. Weakness in one undermines the others. |
Crucially, control activities are not static. In a world of evolving risks—from cyberattacks to ESG reporting challenges—controls must adapt continuously. They must be embedded in technology, aligned with corporate culture, and enforced consistently from the boardroom to the front line. Without them, even the sharpest radar cannot prevent a crash; with them, organizations can convert foresight into resilience, ensuring that risks are not only seen but effectively managed.
What Are COSO Control Activities?
COSO defines control activities as the policies and procedures that help ensure management directives are carried out. They operate at all levels—strategic, tactical, and operational—and across functions.
Examples include:
Segregation of duties
Function: Split responsibilities so that no single person can both initiate and approve transactions.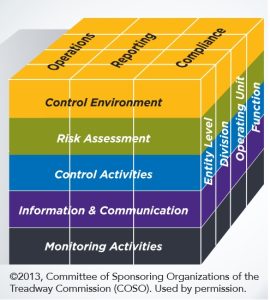
Prevents: Fraud and errors by ensuring every process step is subject to independent oversight.
Authorization and approval procedures
Function: Ensure that significant decisions and expenditures are reviewed and approved by authorized personnel in advance.
Prevents: Unauthorized payments, conflicts of interest, and uncontrolled cost escalation.
IT general controls (access management)
Function: Restrict and monitor who has access to critical systems and data.
Prevents: Data breaches, unauthorized modifications, and cyber fraud.
Reconciliations and exception reporting
Function: Systematically identify discrepancies between records and actual transactions.
Prevents: Errors from remaining undetected and accumulating into material misstatements.
Physical controls (locks, surveillance, inventory counts)
Function: Safeguard physical assets through protection and oversight mechanisms.
Prevents: Theft, loss, or unauthorized use of company resources.
These activities may be preventive (stopping an error before it occurs) or detective (identifying irregularities after the fact). Together, they form the organization’s ability to stay on course when risks materialize.
Case Lessons: When Brakes and Steering Failed
Société Générale – Jérôme Kerviel (2008)
The French bank lost €4.9 billion due to unauthorized trading by Jérôme Kerviel. Controls existed, but segregation of duties was ineffective, allowing him to both create fictitious trades and manage reporting. The brakes were installed but not applied.
Toshiba (2015)
Toshiba overstated profits by over $1.2 billion across seven years. The case revealed weak approval processes and a culture that discouraged employees from challenging directives. Control activities were overridden by management pressure—steering failed under stress.
Volkswagen Emissions Scandal (2015)
VW installed defeat devices to cheat emissions tests. Policies existed, but control activities did not prevent deliberate circumvention. Engineers followed a culture of results-at-any-cost, and oversight mechanisms failed to detect manipulation. This was not a lack of procedures, but a collapse in enforcing them.
These cases illustrate that ineffective control activities can make even the best-designed frameworks meaningless.
The Relationship Between Control Activities and Risk Assessment
Risk assessment identifies what could go wrong; control activities dictate how the organization responds. Without translation into policies and procedures, risk assessments remain theoretical.
For example:
-
Identified cybersecurity risks → lead to multifactor authentication and penetration testing.
-
Identified liquidity risks → lead to daily cashflow monitoring and investment limits.
-
Identified ESG risks → lead to supplier due diligence and third-party audits.
Just as brakes and steering are useless without a driver who reads the road, control activities require a strong control environment and continuous risk assessment to remain effective.
Characteristics of Effective Control Activities
-
Alignment with Objectives
Controls must be designed to support business goals, not create unnecessary bureaucracy. -
Cost-Effectiveness
Controls should mitigate risks at a reasonable cost. Overly complex procedures can paralyze operations. -
Integration with Technology
Automation and IT systems enhance control efficiency but require governance over system access, changes, and data integrity. -
Clarity and Documentation
Controls must be clearly defined, documented, and communicated so employees understand their purpose. -
Adaptability
Controls must evolve with changes in business models, technology, and regulatory environments.
An Also read from the Kansas State University Internal Audit department – Elements of internal control.
Best Practices: Keeping the Vehicle on the Road
Segregation of Duties
Function: Splits responsibilities for initiating, approving, and recording transactions.
Prevents: Fraud or concealment of errors by ensuring no single individual controls all stages of a process.
Authorization and Approval Procedures
Function: Require designated managers to review and authorize significant decisions or payments.
Prevents: Unauthorized expenditures, conflicts of interest, and uncontrolled cost escalation.
Automated Monitoring and Exception Reporting
Function: Use technology to continuously scan for unusual transactions or deviations.
Prevents: Errors or fraud from accumulating unnoticed by flagging issues early for investigation.
IT General Controls (Access and Change Management)
Function: Limit and monitor who can access critical systems and make changes.
Prevents: Data breaches, unauthorized system alterations, and cyber fraud.
Reconciliations
Function: Compare records from different sources (e.g., bank vs. ledger) to ensure accuracy.
Prevents: Misstatements from persisting in financial reporting and operational decision-making.
Physical Controls
Function: Secure physical assets through locks, surveillance, and regular inventory counts.
Prevents: Theft, misuse of resources, or undetected loss of inventory and equipment.
When applied effectively, control activities give organizations agility: they can brake sharply when danger arises and steer confidently through curves.
Challenges in Modern Control Activities
-
Complex IT Environments
Digital transformation expands both opportunities and risks. IT general controls (access, change, backup) are crucial but often neglected. -
Global Operations
Different jurisdictions may require different controls, complicating standardization. -
Management Override
Even the best-designed controls fail if leaders override them. Many scandals are less about missing brakes than about drivers who refused to use them. -
Balancing Efficiency and Control
Too many controls slow decision-making; too few expose the company to unacceptable risks. Finding the right balance is key.
And to go to the extreme – have a look at this Webcast from defensenews.com – THE CHALLENGES OF TESTING COMMAND & CONTROL SYSTEMS.
Conclusion
Control activities are where governance meets execution. They transform the abstract outputs of risk assessment into concrete daily practices. When effective, they are the brakes and steering wheel that keep the organization on course, even on the challenging and curvy roads ahead. When absent, weak, or overridden, companies risk repeating the lessons of Société Générale, Toshiba, or Volkswagen.
Strong control activities require continuous attention: they must be designed, implemented, tested, and adapted. Only then can the organization navigate safely toward its objectives.
In the next article, we will turn to Step 4 – Information & Communication, the nervous system that ensures risk and control information flows freely across the organization and to its stakeholders.
COSO Control Activities
COSO Control Activities
COSO Control Activities COSO Control Activities COSO Control Activities COSO Control Activities COSO Control Activities COSO Control Activities COSO Control Activities COSO Control Activities COSO Control Activities COSO Control Activities